Hipaa Security Risk Assessment Template Free
Hipaa security risk assessment template free - Our risk assessment templates will help you to comply with the following regulations and standards like HIPAA FDA SOX FISMA COOP COG FFIEC. Information security risk assessments serve many purposes some of which include. Steve holds a BSc. Or tap SAQs template library of surveys for regulations like HIPAA Basel 3 and SOX and industry standards like PCI. Once you have developed your policy based on the template be sure to expand it to cover new assets and operations as they are added to your business. Steve Alder has many years of experience as a journalist and comes from a background in market research. The ease at which this all happened surprised me. The interview template allowed me to give them all of the information they needed in less than an hour. Five steps to risk assessment can be followed to ensure that your risk assessment is carried out correctly these five steps are. A vendor risk management questionnaire also known as a third-party risk assessment questionnaire or vendor risk assessment questionnaire is designed to help your organization identify potential weaknesses among your third-party vendors and partners that could result in a data breach data leak or other type of cyber attack.
HIPAA FERPA NY State Cybersecurity Regulations are only some of the laws that require a risk assessment to be done by impacted companies in the healthcare education and financial sectors. Cybersecurity risk assessments help organizations understand control and mitigate all forms of cyber risk. As security compliance and risk management professionals we know that cyber-attacks are increasing in frequency severity and creativity. Create a risk assessment policy that codifies your risk assessment methodology and specifies how often the risk assessment process must be repeated. He is a specialist on legal and regulatory affairs and has several years of experience writing about HIPAA.
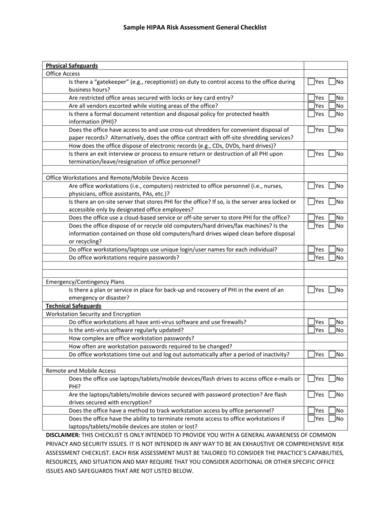
Free 9 Hipaa Security Risk Analysis Templates In Pdf Ms Word
The Disaster Recovery template suite can help in complying with requirements of HIPAA Sarbanes-Oxley SOX FISMA and ISO 27002. Our risk assessment templates will help you to comply with the following regulations and standards like HIPAA FDA SOX FISMA COOP COG FFIEC. Gartner gives a more general definition.
Show ImageHow To Start A Hipaa Risk Analysis Risk Analysis Security Assessment Analysis
If the process of filling out a risk assessment questionnaire is cumbersome this will affect the quality and. Create a risk assessment policy that codifies your risk assessment methodology and specifies how often the risk assessment process must be repeated. Yet many management teams and boards still struggle to grasp the extent to which cyber risks can impact organizational objectives.
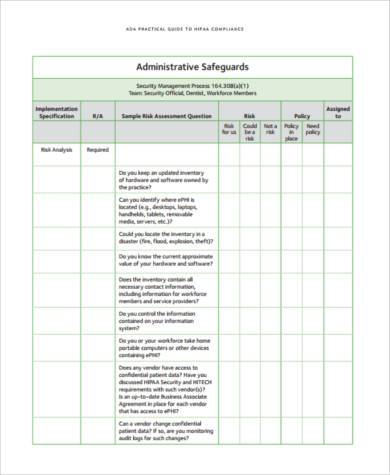
Show ImageAppendix 4 2 Sample Hipaa Security Risk Assessment For A Small Physician Practice Pdf Free Download
Information security risk assessments serve many purposes some of which include. He is a specialist on legal and regulatory affairs and has several years of experience writing about HIPAA. Yet many management teams and boards still struggle to grasp the extent to which cyber risks can impact organizational objectives.
Show ImageAppendix 4 2 Sample Hipaa Security Risk Assessment For A Small Physician Practice Pdf Free Download
Steve Alder has many years of experience as a journalist and comes from a background in market research. Or tap SAQs template library of surveys for regulations like HIPAA Basel 3 and SOX and industry standards like PCI. HIPAA Certification for Employees Company and Products As per The Department of Health and Human Services DHHS which manages and is responsible for enforcing Health Insurance Portability and Accountability Act HIPAA Rule there is no company entrusted to certify an individual as HIPAA Certified or companies or products getting official HIPAA Certification.
Show Image7 Hipaa Security Risk Analysis Examples Pdf Examples
The ease at which this all happened surprised me. This Disaster Recovery Plan DRP template suite can be used as a Disaster Planning Business Continuity Plan BCP by any organization. In this article we will explore how to create a strong vulnerability.
Show ImageFree 7 Sample Security Risk Assessment Forms In Pdf Ms Word
The data security policy template below provides a framework for assigning data access controls. He is a specialist on legal and regulatory affairs and has several years of experience writing about HIPAA. From the University of Liverpool.
Show ImageFree 9 Hipaa Security Risk Analysis Templates In Pdf Ms Word
The potential for an unplanned negative business outcome involving the failure or misuse of IT. The complete package has Risk Assessment guidelines matrix templates forms worksheets policies procedures methodologies tools recovery plan information on free resources and standards. It can be.
Show Image7 Hipaa Security Risk Analysis Examples Pdf Examples
How to do a risk assessment. It is a critical component of risk management strategy and data protection efforts. A vital advantage for security professionals is the ability to come up with robust vulnerability assessment reports.
Show ImageHollandhart Com
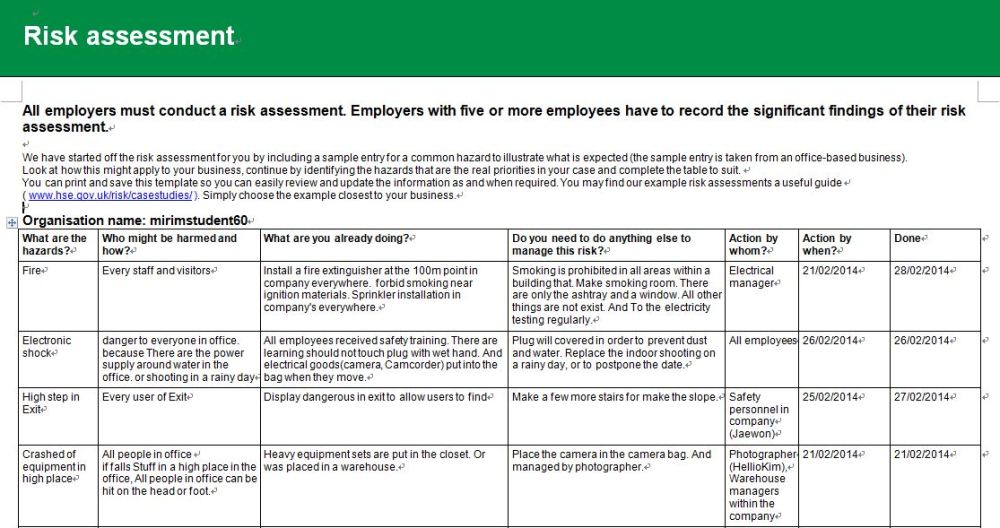
How to do a risk assessment. Five steps to risk assessment can be followed to ensure that your risk assessment is carried out correctly these five steps are. The complete package has Risk Assessment guidelines matrix templates forms worksheets policies procedures methodologies tools recovery plan information on free resources and standards.
Show ImageFree 9 Hipaa Security Risk Analysis Templates In Pdf Ms Word
It does not mean that you are compliant but that you have been taught the terms of the Health Insurance Portability and Accountability Act and also. How to do a risk assessment. Once you have developed your policy based on the template be sure to expand it to cover new assets and operations as they are added to your business.
Show ImageIt is a critical component of risk management strategy and data protection efforts. He is a specialist on legal and regulatory affairs and has several years of experience writing about HIPAA. This Disaster Recovery Plan DRP template suite can be used as a Disaster Planning Business Continuity Plan BCP by any organization. The interview template allowed me to give them all of the information they needed in less than an hour. As security compliance and risk management professionals we know that cyber-attacks are increasing in frequency severity and creativity. The Institute of Risk Management defines a cyber risk as any risk of financial loss disruption or damage to the reputation of an organization from some sort of failure of its information technology systems. Being HIPAA certified means that you have successfully undergone a course designed to train and teach you the information you need to enable your business or organization to become HIPAA compliant. Risk assessments are nothing new and whether you like it or not if you work in information security you are in the risk management businessAs organizations rely more on information technology and. What is a HIPAA Violation. Assess business process risk from third parties and internal teams.
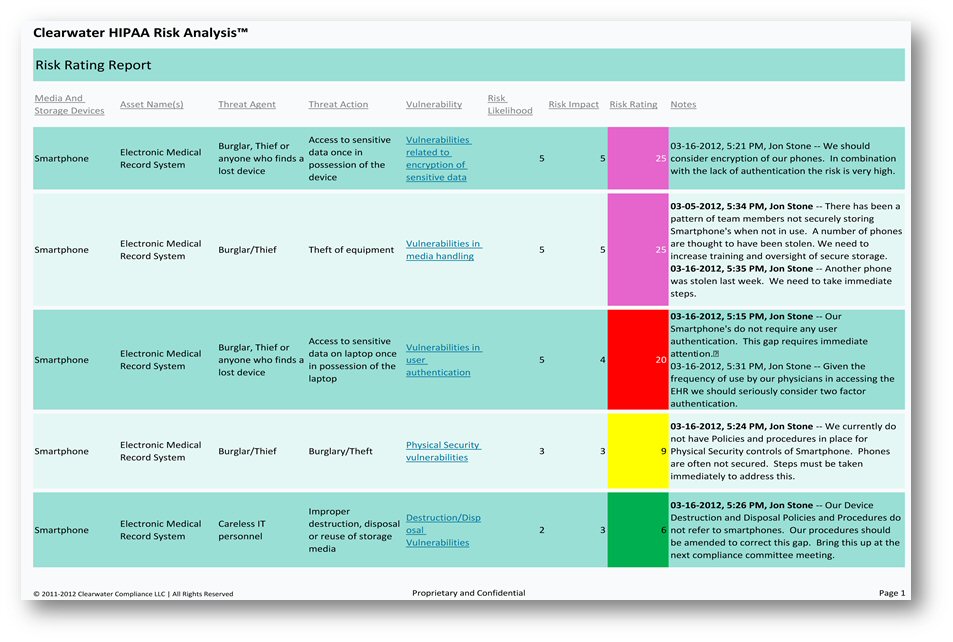
The establishment maintenance and continuous update of an Information Security Management System ISMS provide a strong indication that a company is using a systematic approach for the identification assessment and management of information security risks. Were working hard every day to ensure that cybersecurity risk receives adequate attention in our organizations. Or tap SAQs template library of surveys for regulations like HIPAA Basel 3 and SOX and industry standards like PCI. Steve Alder has many years of experience as a journalist and comes from a background in market research. Use this risk assessment matrix to conduct a qualitative risk analysis of risk probability and gauge how severe the impact of each risk would be on project scope schedule budget and completion. Our risk assessment templates will help you to comply with the following regulations and standards like HIPAA FDA SOX FISMA COOP COG FFIEC. A vital advantage for security professionals is the ability to come up with robust vulnerability assessment reports. What is a cyber risk IT risk definition. In this article we will explore how to create a strong vulnerability. Cybersecurity risk assessments help organizations understand control and mitigate all forms of cyber risk.
Yet many management teams and boards still struggle to grasp the extent to which cyber risks can impact organizational objectives. A risk assessment helps your organization ensure it is compliant with HIPAAs administrative physical and technical safeguardsA risk assessment also helps reveal areas where your organization. Decide who might be harmed. A vendor risk management questionnaire also known as a third-party risk assessment questionnaire or vendor risk assessment questionnaire is designed to help your organization identify potential weaknesses among your third-party vendors and partners that could result in a data breach data leak or other type of cyber attack. The regulation concerns just about everyone that works with PHI. Watch our recorded webinar on IT risk assessment to learn how Netwrix Auditor can help you identify and prioritize your IT risks and know what steps to take to remediate them. Five steps to risk assessment can be followed to ensure that your risk assessment is carried out correctly these five steps are. A risk assessment gives you a concrete list of vulnerabilities you can take to upper-level management and leadership to illustrate the need for additional resources and budget to shore up your information security processes and tools. Risk management for healthcare organizations helps to ensure the all businesses are compliant with HIPAA requirements and outlines potential risks that could occur in a healthcare organization such as clinical testing errors hospital facilities issues security breaches of protected health information PHI and more. Practice shall conduct an accurate and thorough risk analysis to serve as the basis for Practices HIPAA Security Rule compliance efforts.